BCA 01 (Computer Fundamentals and
Pc Software)
Answer
all the Question (3 x5 =15) (Each answer will be 150 Words)
1.
Explain the futures of Multiprogramming Operating System
Answer:
The
multiprogramming operating system.
The multiprogramming operating system can execute several jobs concurrently by switching the attention of the CPU back and forth among them. This switching is usually prompted by a relative slow input, output storage request that can be handled by a buffer, spooler or channel freeing the CPU to continue processing .
The multiprogramming operating system can execute several jobs concurrently by switching the attention of the CPU back and forth among them. This switching is usually prompted by a relative slow input, output storage request that can be handled by a buffer, spooler or channel freeing the CPU to continue processing .
Multiprogramming
makes efficient use of the CPU by overlapping the demands for the CPU and its
I/O devices from various users. It attempts to increase CPU utilization by
always having something for the CPU to execute.
The primary reason multiprogramming operating system was developed and the reason they are popular, is that they enable the CPU to be utilized more efficiently. If the operating system can quickly switch the CPU to another task whenever the being worked in requires relatively slow input, output or storage operations, then CPU is not allowed to stand idle.
Future of multiprogramming operating system:
i) It increases CPU utilization.
ii) It decreases total read time needed to execute a job.
iii) It maximizes the total job throughput of a computer.
The primary reason multiprogramming operating system was developed and the reason they are popular, is that they enable the CPU to be utilized more efficiently. If the operating system can quickly switch the CPU to another task whenever the being worked in requires relatively slow input, output or storage operations, then CPU is not allowed to stand idle.
Future of multiprogramming operating system:
i) It increases CPU utilization.
ii) It decreases total read time needed to execute a job.
iii) It maximizes the total job throughput of a computer.
Example: three jobs are submitted
Almost no contention for resources
All 3 can run in minimum time in a multitasking environment (assuming JOB2/3 have enough CPU time to keep their I/O operations active)
Almost no contention for resources
All 3 can run in minimum time in a multitasking environment (assuming JOB2/3 have enough CPU time to keep their I/O operations active)
____________________________________________________________________________________
2.
(i) WHAT IS GUI ?
A graphical user interface (GUI) is a human-computer interface
(i.e., a way for humans to interact with computers) that uses windows, icons
and menus and which can be manipulated by a mouse (and often to a
limited extent by a keyboard as well). GUIs stand in sharp contrast to command line interfaces (CLIs), which use only text and are accessed solely by a keyboard. The most familiar example of a CLI to many people is MS-DOS. Another example is Linux when it is used in console mode (i.e., the entire screen shows text only).
A window is a (usually) rectangular portion of the monitor screen that can display its contents (EXAMPLE: a program, icons, a text file or an image) seemingly independently of the rest of the display screen. A major feature is the ability for multiple windows to be open simultaneously. Each window can display a different application, or each can display different files (e.g., text, image or spreadsheet files) that have been opened or created with a single application.
An icon is a small picture or symbol in a GUI that represents a program (or command), a file, a directory or a device (such as a hard disk or floppy). Icons are used both on the desktop and within application programs. Examples include small rectangles (to represent files), file folders (to represent directories), a trash can (to indicate a place to dispose of unwanted files and directories) and buttons on web browsers (for navigating to previous pages, for reloading the current page, etc.).
Commands are issued in the GUI by using
a mouse, trackball or touchpad to first move a pointer on the screen to, or on
top of, the icon, menu item or window of interest in order to select
that object. Then, for example, icons and windows can be moved by dragging
(moving the mouse with the held down) and objects or programs can be opened by
clicking on their icons.
2.(II)
Explain the Classification of Viruses
Answer:
Computer Viruses are classified according to their
nature of infection and behavior. Different types of computer virus
classification are given below. • Boot Sector Virus: A Boot Sector Virus infects the first sector of the hard drive, where the Master Boot Record (MBR) is stored. The Master Boot Record (MBR) stores the disk's primary partition table and to store bootstrapping instructions which are executed after the computer's BIOS passes execution to machine code. If a computer is infected with Boot Sector Virus, when the computer is turned on, the virus launches immediately and is loaded into memory, enabling it to control the computer.
• File Deleting Viruses: A File Deleting Virus is designed to delete critical files which are the part of Operating System or data files.
• Mass Mailer Viruses: Mass Mailer Viruses search e-mail programs like MS outlook for e-mail addresses which are stored in the address book and replicate by e-mailing themselves to the addresses stored in the address book of the e-mail program.
• Macro viruses: Macro viruses are written by using the Macro programming languages like VBA, which is a feature of MS office package. A macro is a way to automate and simplify a task that you perform repeatedly in MS office suit (MS Excel, MS word etc). These macros are usually stored as part of the document or spreadsheet and can travel to other systems when these files are transferred to another computers.
• Polymorphic Viruses: Polymorphic Viruses have the capability to change their appearance and change their code every time they infect a different system. This helps the Polymorphic Viruses to hide from anti-virus software.
• Armored Viruses: Armored Viruses are type of viruses that are designed and written to make itself difficult to detect or analyze. An Armored Virus may also have the ability to protect itself from antivirus programs, making it more difficult to disinfect.
• Stealth viruses: Stealth viruses have the capability to hide from operating system or anti-virus software by making changes to file sizes or directory structure. Stealth viruses are anti-heuristic nature which helps them to hide from heuristic detection.
• Polymorphic Viruses: Polymorphic viruses change their form in order to avoid detection and disinfection by anti-virus applications. After the work, these types of viruses try to hide from the anti-virus application by encrypting parts of the virus itself. This is known as mutation.
• Retrovirus: Retrovirus is another type virus which tries to attack and disable the anti-virus application running on the computer. A retrovirus can be considered anti-antivirus. Some Retroviruses attack the anti-virus application and stop it from running or some other destroys the virus definition database.
• Multiple Characteristic
viruses: Multiple Characteristic viruses has different characteristics
of viruses and have different capabilities.
3.
I) write Short notes on Mail Merge ?
Answer:
A mail merge is a method of taking data from a database, spreadsheet, or
other form of structured data, and inserting it into documents such as letters,
mailing labels, and name tags. It usually requires two files, one storing the
variable data to be inserted, and the other containing both the instructions
for formatting the variable data and the information that will be identical
across each result of the mail merge.For example, in a form letter, you might include instructions to insert the name of each recipient in a certain place; the mail merge would combine this letter with a list of recipients to produce one letter for each person in the list.
You can also print a set of mailing labels or envelopes by doing a mail merge. For labels, for example, you would construct a source document containing the addresses of the people you wish to print labels for and a main document that controls where each person's name, address, city, state, and zip code will go on the label. The main document would also contain information about how many labels are on a page, the size of each label, the size of the sheet of paper the labels are attached to, and the type of printer you will use to print the labels. Running a mail merge with the two files results in a set of labels, one for each entry in the source document, with each label formatted according to the information in the main document.
Most major word processing packages
(e.g., Microsoft Word) are capable of performing a mail merge.
Answer the Following: (1 X10)
With 300 Words
1.Explain the Network
Architecture of OSI reference Model ?
The
open systems interconnection (OSI)
model is a product of the open systems interconnection effort at the
international organization for standardisation.
OSI - An
architectural model for open networking systems that was developed by the
International Organization for Standardization (ISO) in Europe in 1974. The
Open Systems Interconnection (OSI) reference model was intended as a basis for
developing universally accepted networking protocols, but this initiative
essentially failed for the following reasons:
- The standards process was relatively closed compared with the open standards process used by the Internet Engineering Task Force (IETF) to develop the TCP/IP protocol suite.
- The model was overly complex. Some functions (such as connectionless communication) were neglected, while others (such as error correction and flow control) were repeated at several layers.
- The growth of the Internet and TCP/IP—a simpler, real-world protocol model—pushed the OSI reference model out.
The
OSI reference model is best seen as an idealized model of the logical
connections that must occur in order for network communication to take place.
Most protocol suites used in the real world, such as TCP/IP, DECnet, and
Systems Network Architecture (SNA), map somewhat loosely to the OSI reference
model. The OSI model is a good starting point for understanding how various
protocols within a protocol suite function and interact.
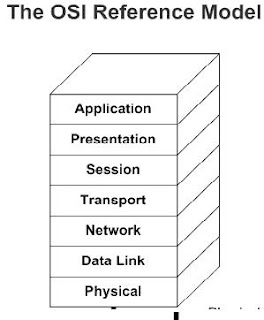
The
OSI reference model has seven logical layers, as shown in the following table.
It
is a characterising and standardizing the functions of communications system in
terms of abstraction layers.
The following figure shows the network
architecture of OSI reference model.
|
Layer Name
|
Description
|
|
|
7
|
Application layer
|
Interfaces user applications with
network functionality, controls how applications access the network, and
generates error messages. Protocols at this level include HTTP, FTP, SMTP,
and NFS.
|
|
6
|
Presentation layer
|
Translates data to be transmitted by
applications into a format suitable for transport over the network.
Redirector software, such as the Workstation service for Microsoft Windows
NT, is located at this level. Network shells are also defined at this layer.
|
|
5
|
Session layer
|
Defines how connections can be
established, maintained, and terminated. Also performs name resolution
functions.
|
|
4
|
Transport layer
|
Sequences packets so that they can be
reassembled at the destination in the proper order. Generates acknowledgments
and retransmits packets. Assembles packets after they are received.
|
|
3
|
Network layer
|
Defines logical host addresses such as
IP addresses, creates packet headers, and routes packets across an
internetwork using routers and Layer 3 switches. Strips the headers from the
packets at the receiving end.
|
|
2
|
Data-link layer
|
Specifies how data bits are grouped
into frames, and specifies frame formats. Responsible for error correction,
flow control, hardware addressing (such as MAC addresses), and how devices
such as hubs, bridges, repeaters, and Layer 2 switches operate., the logical
link control (LLC) layer and the media access control (MAC) layer.
|
|
1
|
Physical layer
|
Defines network transmission media,
signaling methods, bit synchronization, architecture (such as Ethernet or
Token Ring), and cabling topologies. Defines how network interface cards
(NICs) interact with the media (cabling).
|

Thank you very much for the help
ReplyDelete